Message in the Bottle
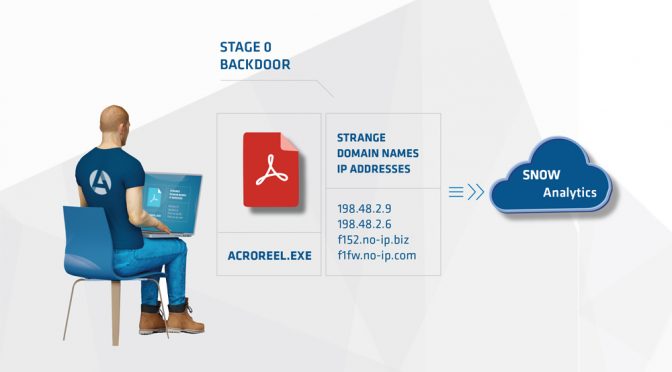
1) While performing the initial base lining of the network on a new client, analysts encountered a set of binaries on a system administrator’s laptop.
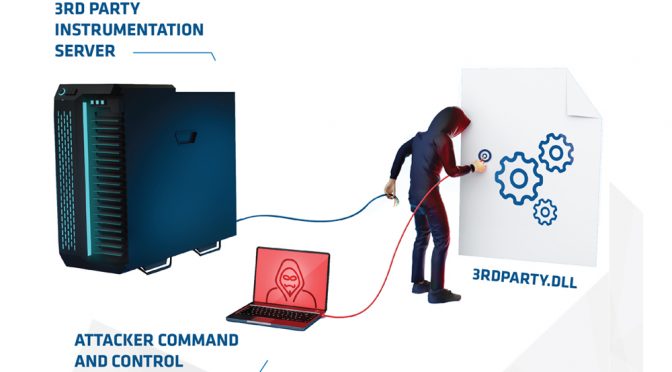
2) The binaries referred to a very common product’s usage instrumentation mechanism, loading the legitimate API DLL found on the system used to generate and transfer the usage data.
3) The usage interface can provide arbitrary instrumentation to be sent in a standardized way to a few HTTP endpoints owned and operated by the product’s company.
4) The binaries found on the system looked in all ways possible to be legitimate and from the product itself. However, they were not signed and no references to the names or hashes could be found online.
5) Through reverse engineering of the binaries, Arc4dia analysts were able to identify the provider included keylogging information into the stream sent to the endpoints. The data stream was also configured to be sent over HTTP (not HTTPS).
6) The conclusion of the analysis was that this set of binaries were left behind after an attack that had occurred a year previously. Its goal was to provide a highly covert method of enabling future operations by the enemy in the event they lost their foothold onto the network. The key strokes were likely going to be collected either through some access in between the client and product’s company or by doing DNS manontheside attacks when necessary to redirect the data stream to an enemy controlled server.
Arc4dia analysts immediately issued a command to delete the file and contacted the client to explain the situation.